Traefik Enterprise Edition 2
Twice The High Availability, Scalability, and Security

Four months after we launched Traefik v2.0, we're happy to announce that the Enterprise Edition is now available, and it is loaded with Enterprise specific features!
On top of enabling our users to leverage the 2.1 feature set (TCP routing, middleware, canary, mirroring, enhanced rule syntax, etc.), the Enterprise Edition keeps helping our customers to set up highly available, scalable, and distributed systems.
What's in TraefikEE 2.0?
Improved High Availability
One of the core values behind Traefik Enterprise Edition is to secure our customers' infrastructure with a highly available solution. Behind the scenes, this is achieved through the Raft consensus algorithm that allows recovery from component failure.
But we know from experience, that in some extreme scenarios which combine heavy network latency, multiple failures, and scheduled operations, the quorum of normal state can be lost.
For this very reason, with TraefikEE 2.0 we've improved the resilience to a temporary quorum loss, and we've introduced a mechanism to enable the cluster to recover – without any downtime – from a single working instance of the controllers, and all it takes is a single command line.
LDAP Authentication
Deploying APIs on your cluster often comes with the necessity to manage credentials, either for your business partners or for your teams. And the more APIs you deploy, the more you engage in microservice architectures, the more API management becomes part of your workflow.
With TraefikEE, we've introduced a way to simplify and centralize authentication with the ability to connect with an LDAP server.
Declare users, groups, and credentials in your directory, then have TraefikEE deal with authorization on your behalf.
In the following example, we're connecting TraefikEE to our LDAP server. Then we attach a rule to our service so that only users from the authorized group (with the group id 500) can use our API.
# Static Configuration
authSources:
mySource:
ldap:
url: ldap://ldap.server.addr:389
version: '3.4'
services:
whoami:
image: containous/whoami
deploy:
labels:
# Dynamic Configuration
- "traefik.http.routers.whoami.rule=Path(`/whoami`)"
- "traefik.http.routers.whoami.service=whoami"
- "traefik.http.services.whoami.loadbalancer.server.port=80"
- "traefik.http.routers.whoami.middlewares=mymiddleware"
- "traefik.http.middlewares.mymiddleware.plugin.ldapauth.source=mySource"
- "traefik.http.middlewares.mymiddleware.plugin.ldapauth.baseDN=dc=example,dc=org"
- "traefik.http.middlewares.mymiddleware.plugin.ldapAuth.searchFilter=(&(objectClass=inetOrgPerson)(gidNumber=500)(uid=%s))"
Customization Made Easy
The premise with TraefikEE is that you can setup a cluster of Traefik in one single command line, saving you hours of configuration decisions. But since no infrastructure is the same, some users needed a way to customize many aspects of their architecture during installation.
TraefikEE 2.0 still comes with a default setup command and it's now possible to generate a pre-configured manifest before the actual installation. With this manifest, users are able to see every available configuration option and tweak every parameter.
Of course, each manifest is specific to the orchestrator, whether you use Swarm or Kubernetes.
Dynamic TLS Certificates Management
TraefikEE has always been fully integrated with Let’s Encrypt, which has enabled many users to automate certificate generation throughout their cluster.
But operating a cluster with many applications also means you have to deal with other certificates, whether in-house or bought separately. For such situations, TraefikEE comes with a command line to deploy them dynamically.
In the following example, we’re adding a whoami.example.com certificate to the cluster.
$ teectl create tls-cert --cert=mycrt.pem --key=mykey.prem
$ teectl get tls-cert
ID CN SANs NOT AFTER STORE DEFAULT
u7vxw whoami.example.com 2022-01-22T15:27:25Z default false
CLI 2.0
Operating a Traefik cluster means being able to operate, configure, re-configure, stop and start proxies at will, wherever they are hosted in your infrastructure -- and TraefikEE embeds a CLI (teectl) for this purpose.
We saw the command line growing to become the main user interface for administrators, and decided it was time to tweak its grammar for more consistency.
Now (like in Kubernetes), you’ll create, get or delete resources to and from your TraefikEE cluster, like in the previous TLS example.
Redesigned Web UI
Inspired by Traefik, the Web UI allows users to have an overview of their cluster's health with just a glance.
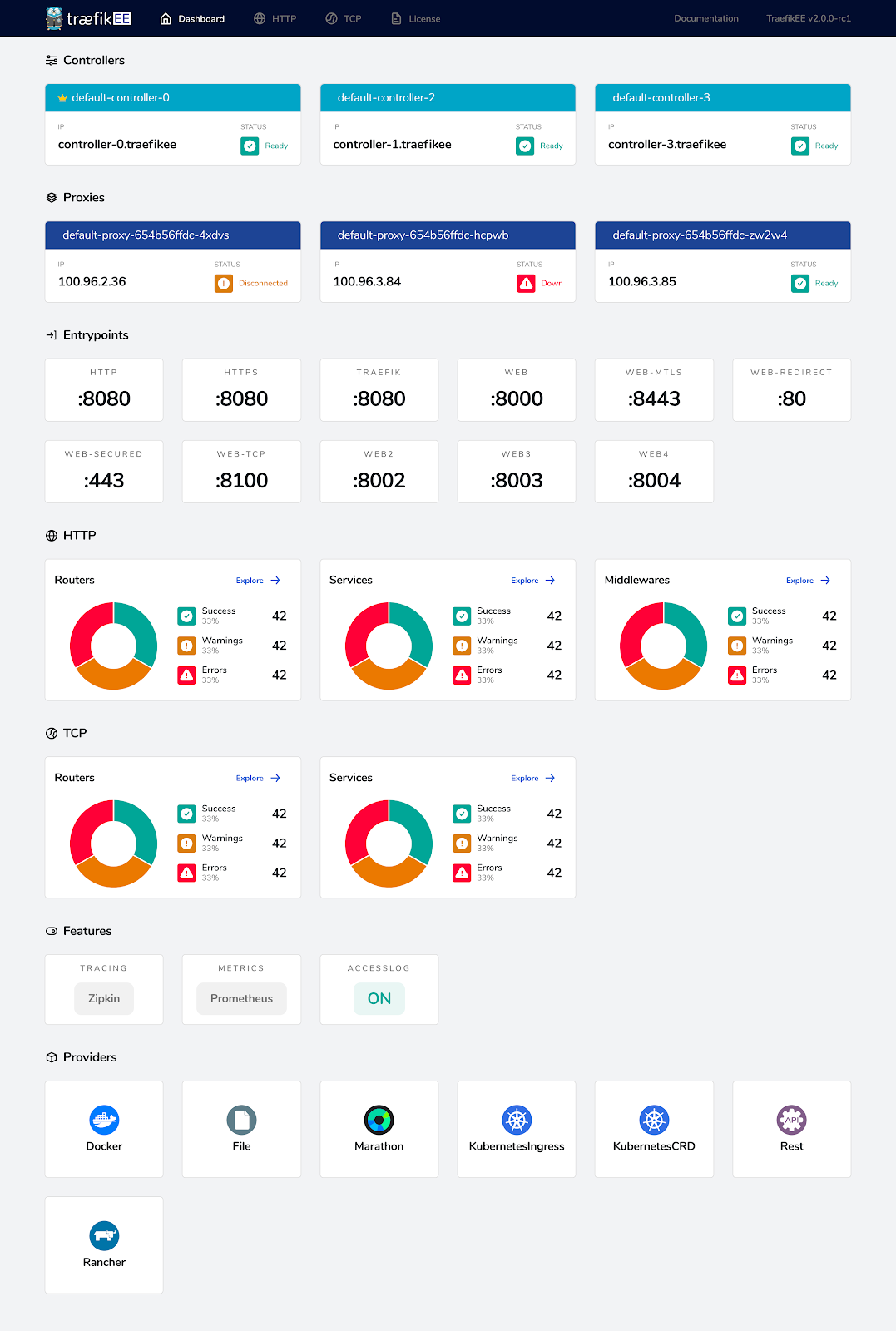
The welcome page contains all the main information. It's the starting point from which you’ll access all the cluster details.
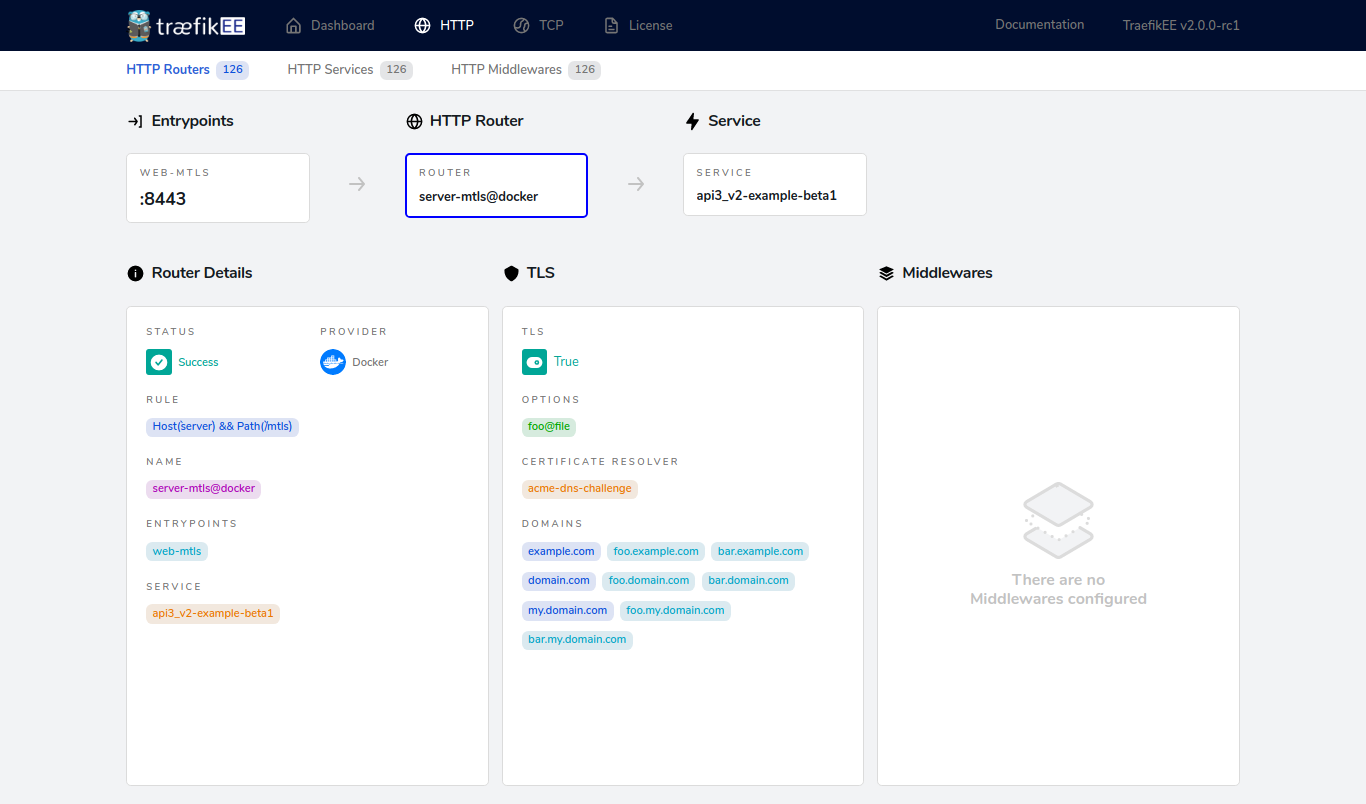
What's Next?
As you can see, TraefikEE not only adds a clustering system on top of Traefik, but it contains additional features designed for enterprise and a CLI to operate the cluster.
There are many benefits you can get from switching to TraefikEE, and the best is that you can test it for yourself and request a free trial license on our website (and to make it simple, the TraefikEE configuration is fully compatible with your existing Traefik configuration).
And if you still have questions or need help finding a tailored option for your infrastructure, we’ll be happy to discuss it with you, and to help you find the best solution for your use case.
Try it today, and be sure that we'll continue to pack TraefikEE with new features driven by companies' needs... to make networking boring!



