Traefik Enterprise and Cloudflare 101

Traefik Enterprise is a unified cloud native networking solution that eases microservices networking complexity.
And what better way to ease the complexity of networking other than taking care of the undeniably tedious task that is managing HTTPS certificates.
In this 101 guide, I will show you how to install the latest version of Traefik Enterprise and how to configure a provider. With my configuration, your Traefik Enterprise automatically will get Let's Encrypt certificates and all certificate requests are validated against Cloudflare DNS.
You can find all the files for Traefik Enterprise on GitHub.
Prerequisites
To follow through with this guide, you need to have the following:
- Kubernetes Cluster
- Traefik Enterprise License Key
- Cloudflare Account
Now that you have everything set up, let's get started!
Configuration
Since version 2.3.0 of Traefik Enterprise, you are able to install it without any additional tool. You can now deploy Traefik Enterprise with Argo CD or some other Continuous Delivery tool.
But first, you need to prepare all the Kubernetes objects.
Namespace
Create a new namespace for your installation with the CLI.
kubectl create namespace traefikee
Or with a file:
---
apiVersion: v1
kind: Namespace
metadata:
name: traefikee
Secret (license)
Add the license as a secret from kubectl. For this example, I am using the Traefik Enterprise license.
kubectl create secret generic traefik-enterprise-license --from-literal=license=EXAMPLE-LICENSE -n traefikee
Or with a file:
---
apiVersion: v1
kind: Secret
type: Opaque
metadata:
name: traefik-enterprise-license
namespace: traefikee
stringData:
license: EXAMPLE-LICENSE
Static Configuration
Create a ConfigMap with the static configuration.
---
apiVersion: v1
kind: ConfigMap
metadata:
namespace: traefikee
name: traefik-enterprise-static-config
data:
static.yaml: |
entryPoints:
web:
address: ":80"
http:
redirections:
entryPoint:
to: websecure
scheme: https
permanent: true
websecure:
address: ":443"
api:
dashboard: true
providers:
kubernetescrd: {}
kubernetesingress: {}
certificatesResolvers:
cloudflare:
acme:
email: [email protected]
storage: acme.json
dnsChallenge:
provider: cloudflare
resolvers:
- "1.1.1.1"
You can copy this example in your editor and modify it as you like. Make sure to change the example email address used here.
Manifest
With a simple Curl call, you can get your YAML manifest to deploy all Traefik Enterprise components.
Here's an example of the latest version of Traefik Enterprise:
curl -L -k "https://install.enterprise.traefik.io/v2.6?cluster=traefik-enterprise&namespace=traefikee" -o traefik-enterprise-manifest.yaml
Add environment variables for Cloudflare
First, create a Secret with your login information for Cloudflare API.
---
apiVersion: v1
kind: Secret
metadata:
name: cloudflare-api-credentials
namespace: traefikee
type: Opaque
stringData:
email: YOUR_CLOUDFLARE_EMAIL
apiKey: YOUR_API_TOKEN
Edit the Traefik Enterprise manifest and add the environment variables to the traefik-enterprise-controller statefulSet, just after the license variable definition.
- name: CF_API_EMAIL
valueFrom:
secretKeyRef:
key: email
name: cloudflare-api-credentials
- name: CF_API_KEY
valueFrom:
secretKeyRef:
key: apiKey
name: cloudflare-api-credentials
Install Traefik Enterprise
It's finally time to install Traefik Enterprise!
Argo CD
Take all files and commit them to your Git repo. Now you are able to connect the repository with Argo CD. Create a new App and deploy Traefik Enterprise.
Kubectl
The easiest way to deploy Traefik Enterprise is with kubectl.
kubectl apply -f traefik-enterprise-ns.yaml
kubectl apply -f traefik-enterprise-license-secret.yaml
kubectl apply -f cloudflare-secret.yaml
kubectl apply -f traefik-enterprise-static-configmap.yaml
kubectl apply -f traefik-enterprise-manifest-cloudflare-env.yaml
Wait for all the Traefik Enterprise component to come up.
kubectl get po -n traefikee
NAME READY STATUS RESTARTS AGE
traefik-enterprise-controller-0 1/1 Running 0 21m
traefik-enterprise-plugin-registry-0 1/1 Running 0 22m
traefik-enterprise-proxy-598c694f9d-fdw2f 1/1 Running 0 22m
traefik-enterprise-proxy-598c694f9d-g625t 1/1 Running 3 22m
Operations
Dashboard
To add some basic security to your dashboard, create an HTTP basic auth middleware. Use the following command to create a base64 encoded htpasswd file with traefik as user and enterprise as password:
htpasswd -n -b traefik enterprise | openssl base64
Add your credentials to the secret for basic-auth:
---
apiVersion: v1
kind: Secret
metadata:
name: traefik-enterprise-dashboard-auth
namespace: traefikee
data:
users: |2
dHJhZWZpazokYXByMSR6R2NRa0xLTCRPWDlFQkZkeVhCWjVNZ2hSVEgzYVMxCgo=
Define the basicAuth middleware to use the secret:
---
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: traefik-enterprise-dashboard-basicauth
namespace: traefikee
spec:
basicAuth:
secret: traefik-enterprise-dashboard-auth
Create an ingress route to the service api@internal to enable the dashboard. Here, make sure to change the matching host rule.
---
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: traefik-enterprise-dashboard
namespace: traefikee
spec:
entryPoints:
- websecure
routes:
- match: Host(`dashboard.example.com`)
kind: Rule
services:
- name: api@internal
kind: TraefikService
middlewares:
- name: traefik-enterprise-dashboard-basicauth
tls:
certResolver: cloudflare
Apply the files with kubectl:
kubectl apply -f traefik-enterprise-basicAuth-secret.yaml
kubectl apply -f traefik-enterprise-dashboard-middleware.yaml
kubectl apply -f traefik-enterprise-dashboard-igr.yaml
And done! You can now connect to the dashboard in your browser with the URL you define in the ingressRoute.
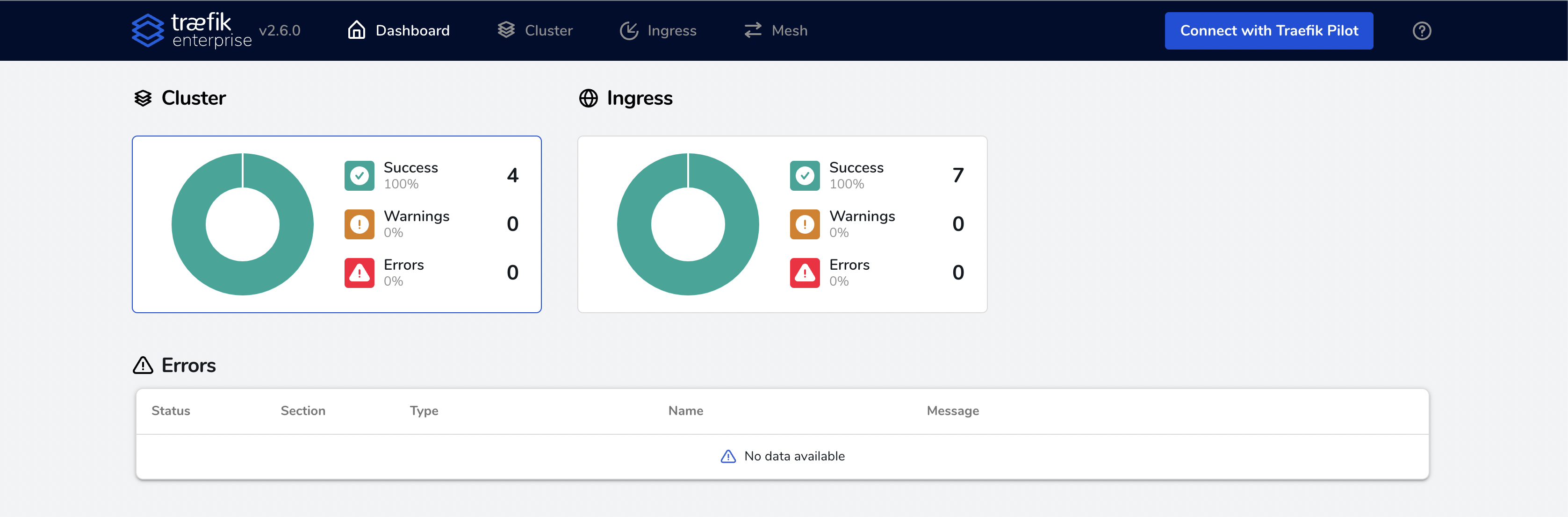
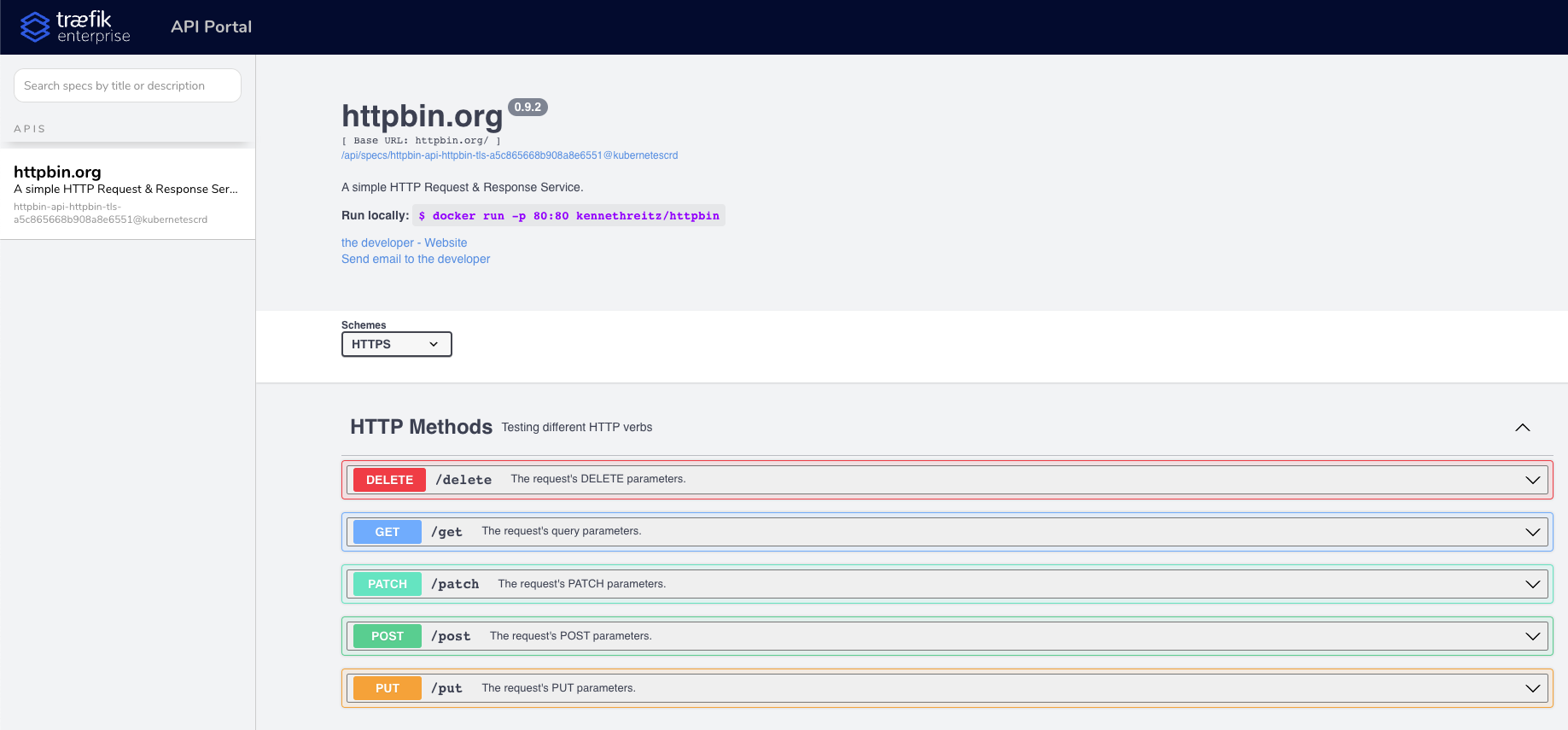
API Portal
The API Portal groups all of the API specifications from your services into a web UI. Currently, Traefik Enterprise supports OpenAPI.
Add these two lines to your static configuration, to enable API Portal.
apiportal:
path: spec.json
Create an ingress route to the service apiportal@internal to enable the API Portal dashboard. Don't forget to change the matching host rule here as well.
---
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: traefik-enterprise-api
namespace: traefikee
spec:
entryPoints:
- websecure
routes:
- match: Host(`apiportal.example.com`)
kind: Rule
services:
- name: apiportal@internal
kind: TraefikService
tls:
certResolver: cloudflare
Note: I would recommend that you added the Basic Auth middleware to your API. Otherwise, anyone can access your API Portal web UI without any authentication.*
Traefik Enterprise now searches every service. If there is a service detected which supports the OpenAPI format and can be reached under the path /api/swagger.json, this service will be listed in the API portal.
Example spec.json
Here is an example of an OpenAPI supported service.
---
apiVersion: v1
kind: Namespace
metadata:
name: httpbin
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: api-httpbin
namespace: httpbin
spec:
replicas: 1
selector:
matchLabels:
app: api-httpbin
template:
metadata:
labels:
app: api-httpbin
spec:
containers:
- name: whoami
image: kennethreitz/httpbin
---
apiVersion: v1
kind: Service
metadata:
name: api-httpbin
namespace: httpbin
labels:
app: api-httpbin
spec:
type: ClusterIP
ports:
- port: 80
name: api
selector:
app: api-httpbin
---
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: api-httpbin-tls
namespace: httpbin
spec:
entryPoints:
- websecure
routes:
- kind: Rule
match: Host(`httpbin.example.com`)
services:
- name: api-httpbin
port: 80
tls:
certResolver: cloudflare
Make sure to change the host values and then apply this files:
kubectl apply -f traefik-enterprise-static-configmap-apiportal.yaml
kubectl apply -f traefik-enterprise-apiportal-igr.yaml
kubectl apply -f traefik-enterprise-petstore-api.yaml
You can now check the API portal to have a look at your API.
Connect with teectl
To get things started, you need to install the teectl command-line tool.
Once your cluster is ready, generate credentials from your cluster using Traefik Enterprise. Generate the credentials on one of your controllers and use teectl to import the cluster credentials.
kubectl exec -n traefikee traefik-enterprise-controller-0 -- /traefikee generate credentials --kubernetes.kubeconfig="${KUBECONFIG}" --cluster=traefik-enterprise > traefikee/config.yaml > config.yaml
Now you can import the cluster configuration to teectl.
teectl cluster import --file="config.yaml"
And finally, select this new cluster.
teectl cluster use --name traefik-enterprise
You can now use teectl to operate your cluster.
Conclusion
Since version 2.3.0, Traefik Enterprise deployment has been made very simple. In a few minutes, you are able to run Traefik Enterprise in our Kubernetes cluster.
I’m really happy to see how Traefik Enterprise is getting better and making your life easier! Always keep an eye on the new releases of Traefik Enterprise for more improvements and new capabilities.




