From Ingress to API Management: How Traefik OSS Grows with You

In the ever-evolving landscape of cloud-native technologies, managing and securing microservices and APIs effectively is crucial for businesses of all sizes. But as your API ecosystem grows and matures, so do your needs.
This blog will guide you through the seamless migration journey across Traefik Labs' comprehensive product portfolio, highlighting the effortless upgrade process that bridges it together. Starting from the foundational Traefik Proxy, you can now elevate your API operations to new heights with the Traefik Hub API Gateway and API Management tools.
And while we’re going to get deep in the weeds, I hope you’ll see the beauty in its simplicity—upgrading Traefik is essentially a replacement of the running binary, making it a non-disruptive process.
Start With Us and Grow With Us
Traefik Labs helps DevOps and Platform engineers throughout their cloud-native operations journeys, from a simple reverse proxy implementation to more advanced API lifecycle management capabilities.
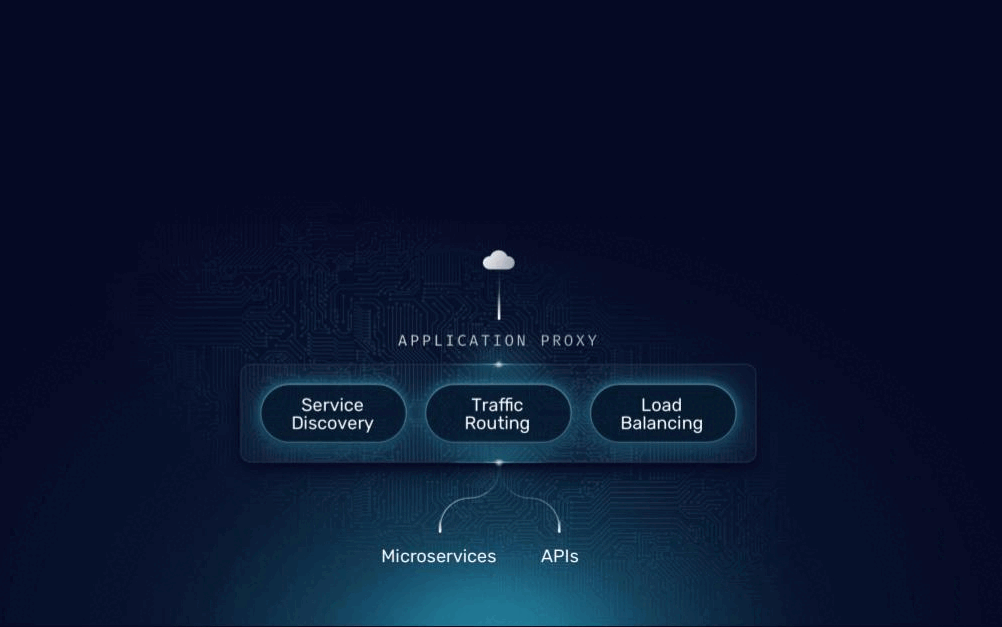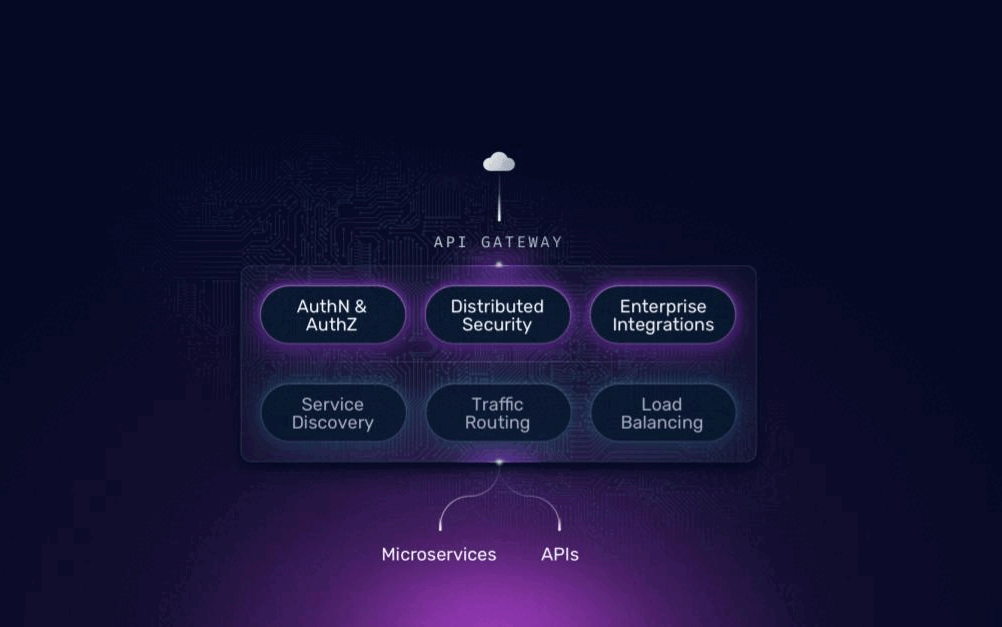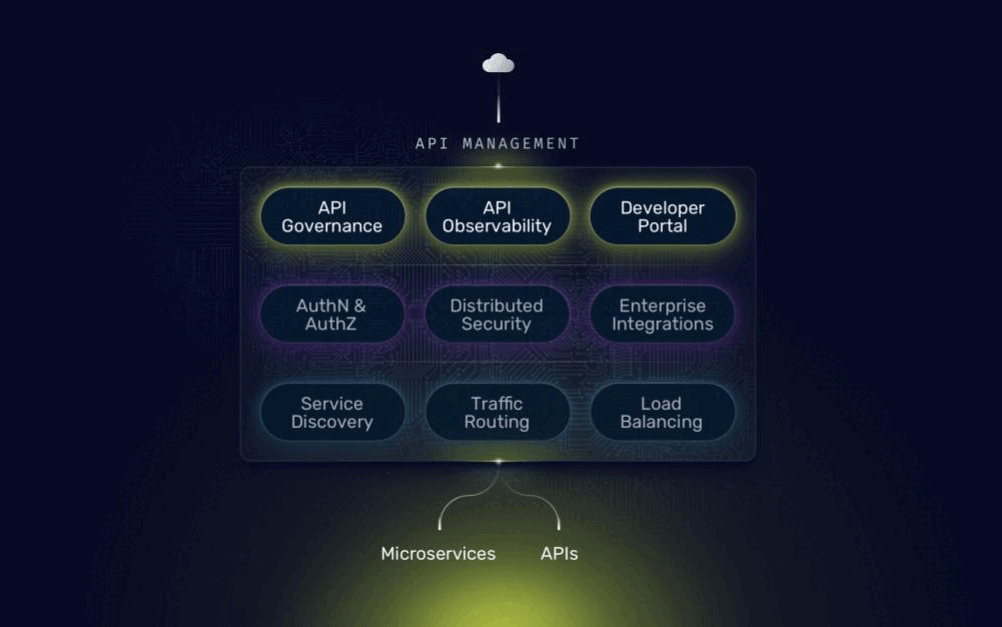
Traefik Hub API Gateway and API Management are built on the open-source Traefik Proxy. They include all the capabilities and characteristics of Proxy and extend it with specialized features targeting APIs. Each level-up takes just a few seconds and is an additive extension, nothing is taken away. Existing configurations and the UX remain the same. Everything you appreciate about Traefik Proxy today is carried through into each upgrade stage.
Since Proxy can run in many different environments, our API Gateway and Management can also publish and secure APIs from every Kubernetes flavor, big cloud providers, Hashicorp Nomad, Docker Swarm, and many more. And all these solutions are based on declarative configuration and GitOps. Leverage labels, middlewares, plugins, and CRDs declaratively, no matter which product you run.
Let’s explore the three journey steps in detail with short hands-on labs, starting with the origins and significance of Traefik Proxy.
Traefik Proxy: Born in The Trenches
The Traefik story began in 2015, addressing a real-world production challenge encountered by Emile Vauge, the founder of Traefik Labs. Deploying thousands of microservices demanded a solution that transcended the limitations of existing reverse proxies at that time. Traditional solutions lacked the automation, service discovery, and scalability required for their environment. This led to the birth of Traefik Proxy, a solution designed from the ground up for the cloud-native world.
Traefik Proxy's focus on ease of use and powerful features quickly propelled it to global recognition. With over 3.3 billion downloads and a place among the top 15 most downloaded images on Docker Hub, Traefik has become a cornerstone of cloud-native infrastructure. This widespread adoption is a testament to its core strengths:
- Simplicity: Declarative configuration and GitOps integration streamline management and ensure infrastructure-as-code best practices.
- Automation: Automatic service discovery and certificate management eliminates manual configuration burdens by automatically detecting and configuring routes to newly deployed services, reducing administrative overhead.
- Scalability: Traefik scales effortlessly alongside your infrastructure, handling even the most demanding workloads.
Its versatility allows deployment on various cloud environments, including all Kubernetes distributions and other container orchestrators like Hashicorp Nomad or Docker Swarm, as well as bare metal and virtual machines, making it a comprehensive solution for all possible scenarios. Traefik serves as the gatekeeper of infrastructure, ensuring security, observability, and efficiency while scaling up to meet evolving needs.
Unsurprisingly, Traefik Proxy is a trusted solution for organizations of all sizes. Financial institutions, major retailers, and countless service providers leverage Traefik to manage mission-critical production workloads. It’s an ideal choice for:
- Users prioritizing best-of-breed integrations: Traefik Proxy integrates seamlessly with a vast ecosystem of tools and technologies, allowing you to leverage your existing infrastructure.
- Environments requiring advanced network routing: Traefik Proxy functions as a versatile application proxy, handling tasks like ingress control, reverse proxying, and load balancing. It also supports content caching and circuit breaking to enhance performance and resilience.
- Organizations seeking a free and open-source solution: Traefik Proxy is a fully open-source project allowing complete transparency and customization. However, you can also get commercial support with 24/7 access to the Traefik Labs team.
Now that it’s clear what Traefik Proxy is and what it can do for you, let’s get our hands dirty and explore the journey of an API in the Traefik ecosystem.
Journey Lab 1: Deploy a Weather Service with Traefik Proxy
In this blog post, apart from covering the obvious upgrade steps from Proxy to API Gateway then to API Management, we’ll follow the life of a simple Weather API for illustration purposes.
The first step with the open-source Traefik Proxy is where everybody gets familiar with the Traefik ecosystem. Let’s deploy a Proxy to simulate the Kubernetes-based infrastructure of our imaginary weather forecasting service provider company.
helm repo add --force-update traefik https://traefik.github.io/charts
helm install traefik -n traefik --create-namespace --wait \
--set ingressClass.enabled=false \
--set ingressRoute.dashboard.enabled=true \
--set ingressRoute.dashboard.matchRule='Host(`dashboard.docker.localhost`)' \
--set ingressRoute.dashboard.entryPoints={web} \
--set ports.web.nodePort=30000 \
--set ports.websecure.nodePort=30001 \
traefik/traefik
k3d cluster create traefik-hub --port 80:80@loadbalancer \
--port 443:443@loadbalancer --port 8000:8000@loadbalancer \
--k3s-arg "--disable=traefik@server:0"
Once it's installed, we can access the local Proxy dashboard: http://dashboard.docker.localhost/
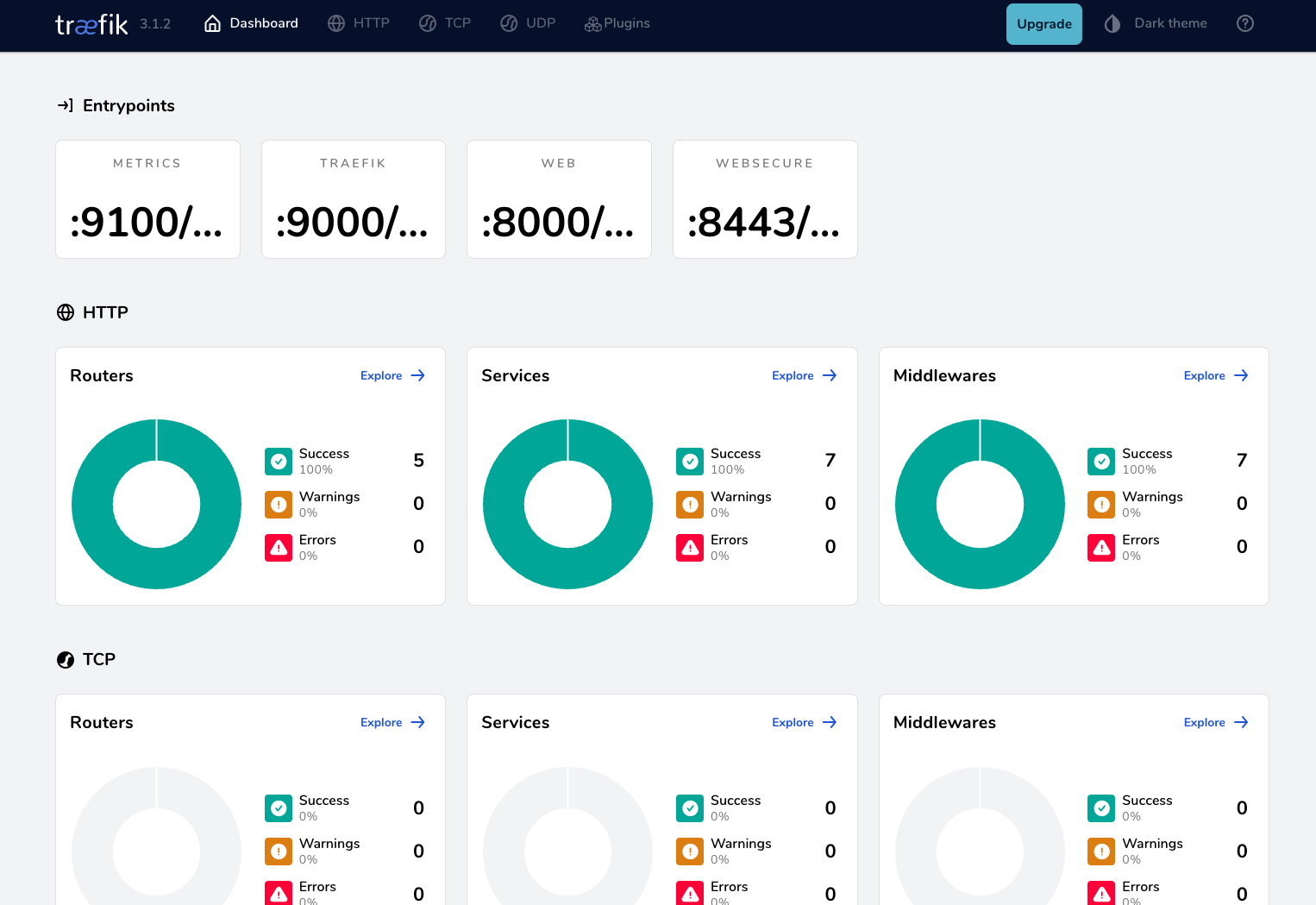
Now, it’s time to deploy the backend of the Weather API using a simple JSON server written in Go and expose it with an IngressRoute object:
kubectl create namespace apps
kubectl apply -f https://raw.githubusercontent.com/traefik/hub/master/src/manifests/weather-app.yaml
kubectl apply -f https://raw.githubusercontent.com/traefik/hub/master/src/manifests/walkthrough/weather-app-no-auth.yaml
The Traefik-native IngressRoute is chosen here for simplicity. Still, Traefik Proxy can also expose applications using the old-standard Kubernetes Ingress or Kubernetes’ new Gateway API HTTPRoute objects. In fact, we have first-class production-ready Kubernetes Gateway API support starting from Proxy v3.1!
The Weather API can be accessed now; let’s try it using curl:
$ curl http://walkthrough.docker.localhost/no-auth
{
"public": [
{ "id": 1, "city": "GopherCity", "weather": "Moderate rain" },
{ "id": 2, "city": "City of Gophers", "weather": "Sunny" },
{ "id": 3, "city": "GopherRocks", "weather": "Cloudy" }
]
}
Let’s not keep the API unsecured; protect it quickly with Basic Authentication.
kubectl apply -f https://raw.githubusercontent.com/traefik/hub/master/src/manifests/walkthrough/weather-app-basic-auth.yaml
# To generate the password, we used `htpasswd -nb foo bar | openssl base64`
# The endpoint path has also moved to /basic-auth
Basic Authentication was widely used in the early days of the web. However, it also has a security risk: credentials can be visible to any observer when using HTTP. Additionally, it uses hard-coded credentials, potentially giving more authorization than required for a specific use case.
Nowadays, those issues are addressed when using JSON Web Tokens (JWT). A JWT can be cryptographically verified; it detaches authentication from user credentials and has an issue and expiration date.
Even in this simple use case, this is how we reach the need for a sophisticated API gateway that has enterprise-level authentication and authorization, among many other new capabilities, on top of Traefik Proxy.
Traefik Hub API Gateway: Level Up Your API Security
While the exact percentage may vary depending on the data source and methodology, recent reports consistently show that API traffic makes up most of the web traffic. Imperva found that 71% of internet traffic in 2023 was API calls. The API Security and Management Report by Cloudflare indicates that APIs accounted for over 57% of dynamic internet traffic processed by their platform in the past year. And according to Akamai, 83% of web traffic consisted of API calls.
The growth in API usage is driven by factors like digital transformation, cloud migration, and the rise of the microservice architecture. As APIs proliferate within organizations, the need for an API Gateway becomes increasingly critical, particularly as centralizing common functionalities to streamline operations and enhance security becomes a priority.
Traefik Hub API Gateway offers a natural evolution from Traefik Proxy, addressing this need by offering a range of enterprise-grade features specifically targeting the use case of exposing and securing APIs. Building upon the core strengths of Proxy, our API gateway equips you with a comprehensive suite of features designed to safeguard your APIs, including centralized authentication and authorization, distributed security features, and various vendor integrations.
- Centralized security and control: Imagine managing authentication and authorization across your entire API portfolio from a single location. Traefik Hub API Gateway empowers you to do just that. It supports a wide range of industry-standard protocols, like OIDC and OAuth token introspection, allowing you to define and enforce access policies for all your APIs centrally. This eliminates the need for repetitive implementation and configuration on the microservice level and ensures consistent security practices across your deployments.
- Distributed security features: Traefik Hub API Gateway takes security a step further by offering features like distributed rate limiting and distributed TLS certificates. Rate limiting ensures that no single API backend becomes overwhelmed by excessive traffic spikes. Rate-limiting quotas are distributed across your Gateway instances, providing a robust defense against denial-of-service attacks. Additionally, API Gateway integrates seamlessly with security tools like Let's Encrypt, allowing you to provision and manage TLS certificates for your APIs effortlessly, even in a distributed environment.
- Enhanced vendor integrations: The modern API landscape often involves a complex ecosystem of tools and services. Traefik Hub API Gateway recognizes this by integrating with leading security vendors like HashiCorp Vault and Azure Key Vault. This enables you to centralize your secrets management and leverage existing security infrastructure within your organization.
- Native Web Application Firewall (WAF): In our API Gateway, the recently announced Coraza WAF integration is implemented natively as part of the Gateway’s code base. The native integration provides more than 23 times (Yes, you read that right!) performance improvement over the plugin-based WAF available in Proxy.
- Open-source with enterprise benefits: Traefik Hub API Gateway retains the open-source core of Traefik Proxy, allowing you to benefit from continuous innovation from the whole open community. However, API Gateway also unlocks additional enterprise-grade features on top of Proxy without requiring excessive migration.
Upgrading from Traefik Proxy to API Gateway is a smooth and straightforward process. The seamless upgrade path protects your investment in existing configurations and ensures minimal disruption to your ongoing operations. All your current configurations can stay in place, and the API Gateway continues to honor them without any change. While building upon the foundation you've established with Traefik Proxy, Traefik Hub API Gateway empowers you to manage access centrally, enforce security policies, and leverage industry-standard best practices.
Journey Lab 2: Upgrade Traefik Proxy to Traefik Hub API Gateway
Let’s continue the upgrade journey in this next lab, leveling up the Weather API game from Proxy to API Gateway capabilities. The upgrade is as easy as setting up a license key and executing a simple Helm chart upgrade. Fill out this form to get a trial or production license key.
Now, open a terminal and save the license as a Kubernetes secret:
kubectl create secret generic license \
--namespace traefik \
--from-literal=token=$TRAEFIK_HUB_TOKEN
Then, upgrade Traefik Proxy to Traefik Hub using the same Helm chart we used previously since Traefik Hub API Gateway is 100% compatible with Traefik Proxy v3 and up. All settings are retained; the only command you need to execute just replaces the running binary with a new one:
helm upgrade traefik -n traefik --wait \
--reuse-values \
--set hub.token=license \
--set image.registry=ghcr.io \
--set image.repository=traefik/traefik-hub \
--set image.tag=v3.2.0 \
traefik/traefik
The upgrade finishes in seconds, and the dashboard is still reachable (http://dashboard.docker.localhost/), but it now shows the Traefik Hub API Gateway logo in the top left corner.
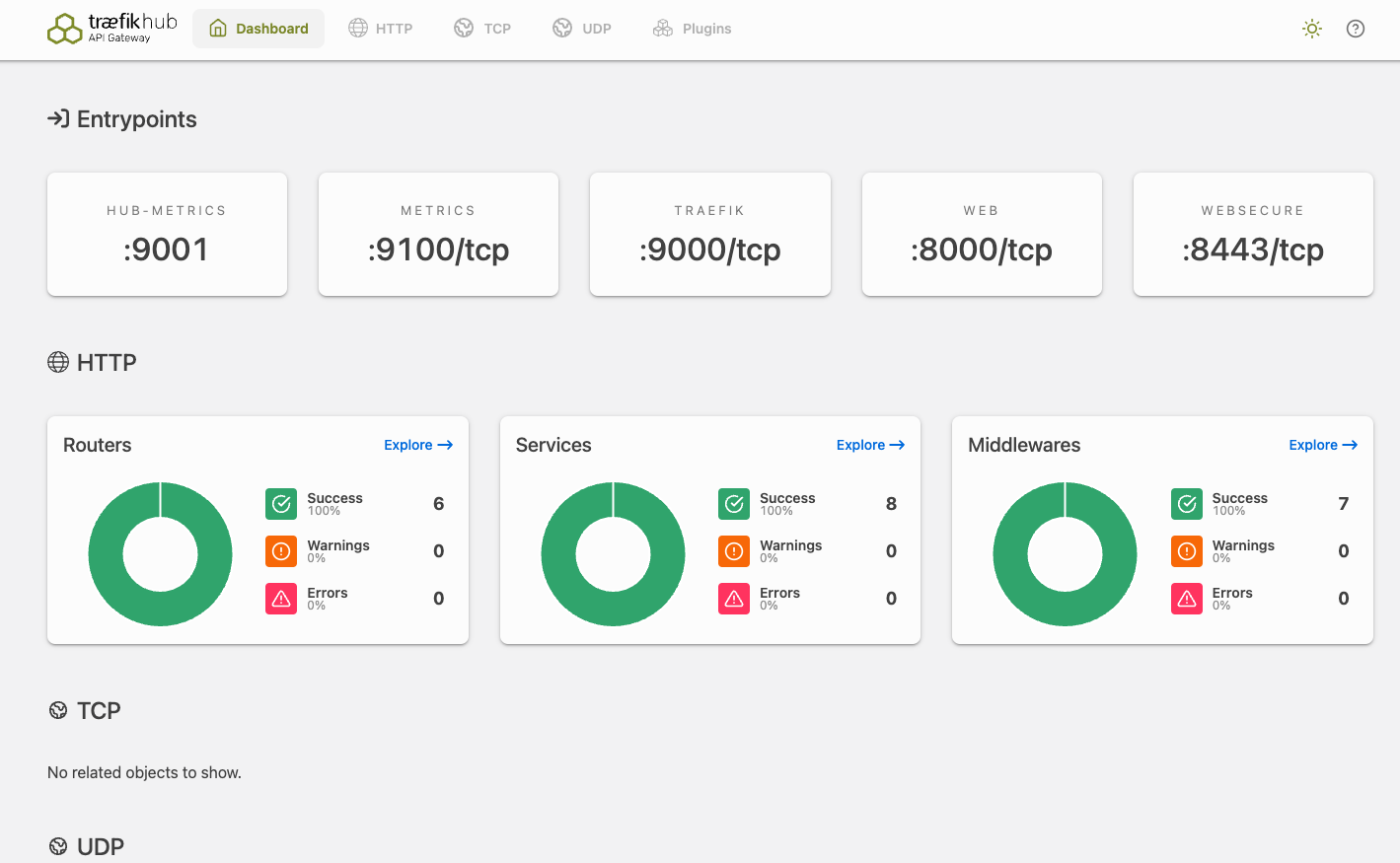
You can also confirm that Basic Auth is still here if you execute the same curl commands against the Weather API. All other configurations are also kept and served.
Let's secure the weather API with something more professional, such as an API Key, a new middleware to which the API Gateway gives access (among many other things).
First, we generate the hash of our API key: “Let's use API Key with Traefik Hub”. Using the key hash in the configuration ensures that the key itself is not leaked, even if it is accidentally pushed to a public Git repository.
htpasswd -nbs "" "Let's use API Key with Traefik Hub" | cut -c 2-
We can now put it into the API Key middleware and apply it:
kubectl apply -f https://raw.githubusercontent.com/traefik/hub/master/src/manifests/walkthrough/weather-app-apikey.yaml
# The API path has also been changed to reflect the use case better, now it’s /api-key
Test it with the following commands:
# This call is not authorized => 401
curl -I http://walkthrough.docker.localhost/api-key
# Let's set API Key
export API_KEY=$(echo -n "Let's use API Key with Traefik Hub" | base64)
# This call with the token is allowed => 200
curl -I -H "Authorization: Bearer $API_KEY" \
http://walkthrough.docker.localhost/api-key
The API is now secured using an API key. The API gateway also allows you to handle users with an identity provider using OIDC or OAuth, apply distributed rate-limiting, and implement other enterprise-grade configurations.
But what if we want to cover internal and external use cases and protect the Weather API on the HTTP verb level to apply further governance? Or test a new API version with part of the production traffic? And what about publishing all the managed APIs to a developer portal for easy discovery and reduced time to consumption?
You’ll need Traefik Hub with API Management features enabled to do this.
Traefik Hub API Management: Granular Control and Scalability
As your API ecosystem scales beyond security needs, managing APIs effectively becomes crucial. Building upon the robust features of Traefik Hub API Gateway, Traefik Hub API Management offers a powerful solution for comprehensive API lifecycle management, enabling you to govern your APIs, streamline development workflows, and cater to diverse API stakeholder needs.
- API governance for complete control: Traefik Hub API Management provides a centralized platform for discovering, registering, and managing your entire API portfolio. Features like versioning and Kubernetes-native API labels and selectors allow you to organize your APIs logically and track their evolution over time. Additionally, API Management integrates with linters, which can automatically detect and flag potential errors within your API configurations before they impact production.
- Advanced API security: API Management takes API security to the next level by offering granular access control mechanisms. You can define fine-grained permissions for individual users or groups, ensuring only authorized users can access specific API resources and functionalities. Furthermore, API Management integrates with industry-standard authentication protocols, allowing you to leverage existing identity and access management (IAM) solutions within your organization.
- API monitoring and observability: Deep insights into API health and performance are crucial for maintaining a reliable and scalable API landscape. Traefik Hub API Management integrates seamlessly with OpenTelemetry, providing comprehensive metrics and tracing capabilities. This allows you to gain real-time visibility into API traffic patterns, identify potential bottlenecks, proactively address any performance issues, and troubleshoot effectively.
- API Developer Portal: Create one or more dedicated API Developer Portals easily! The portal is a central hub for developers to discover, understand, and interact with your APIs. The portal can house API documentation, interactive consoles for testing purposes, and clear instructions on integrating with your APIs. You can also fully customize it to your liking. By providing a user-friendly developer experience, API Management fosters adoption and streamlines the development process for your APIs' internal and external consumers.
As with the previous steps, upgrading from Traefik Proxy or API Gateway to API Management is a similarly simple process. It involves a license upgrade and a Helm chart update, minimizing disruption to ongoing operations. API Management inherits all the functionalities of both Proxy and Gateway, ensuring a smooth transition and continued access to their features. API Management also treats configuration through declarative CRDs as a first-class citizen, but also offers a user-friendly UI for managing API configurations and their current state.
Journey Lab 3: Upgrade Traefik Hub API Gateway to API Management
In our last lab, we assume that the license of the weather provider company has been updated with enabling API Management capabilities. After that, we enable the API Management feature on the Traefik Hub deployment using the same Helm chart:
helm upgrade traefik -n traefik --wait \
--reuse-values \
--set hub.apimanagement.enabled=true \
traefik/traefik
The upgrade was as easy as executing this one command. The local dashboard is still reachable on http://dashboard.docker.localhost/ and we can also confirm that the API is still secured using an API Key.
Now, let's promote the Weather API Ingress to be a managed API with Traefik Hub API Management:
kubectl apply -f https://raw.githubusercontent.com/traefik/hub/master/src/manifests/walkthrough/api.yaml
What did we just do here?
- The applied manifest has created a managed
APICRD describing the properties of the Weather API, like the location of its OpenAPI Specification. - It also created an
API AccessCRD describing who can access the Weather API. - It removed the API Key authentication middleware, as we'll use Traefik Hub's built-in identity provider for user and credential management. The API is still secured, as we'll see it shortly.
- It added a simple one-line annotation on the existing
IngressRouteCRD with a link to theAPICRD created in the 1st point, effectively promoting the ingress to be now a Traefik Hub-managed API.
hub.traefik.io/api: walkthrough-weather-api # <= Link to the API using its name
We can confirm this API is still not publicly exposed without authentication as it returns the expected 401 Unauthorized HTTP code. To be able to consume the API, let’s create a user for this API in the Traefik Hub API Management online dashboard.
The user created previously will connect to an API Portal to generate an API key, so let's deploy our API Portal!
kubectl apply -f https://raw.githubusercontent.com/traefik/hub/master/src/manifests/walkthrough/api-portal.yaml
After a couple of seconds, the API Portal should be reachable on http://api.walkthrough.docker.localhost. Log in with the admin user and create an API Key. The Weather API is now consumable with the new token, and it��’s also visible on the portal:
curl -H "Authorization: Bearer $ADMIN_TOKEN" \
http://api.walkthrough.docker.localhost/weather
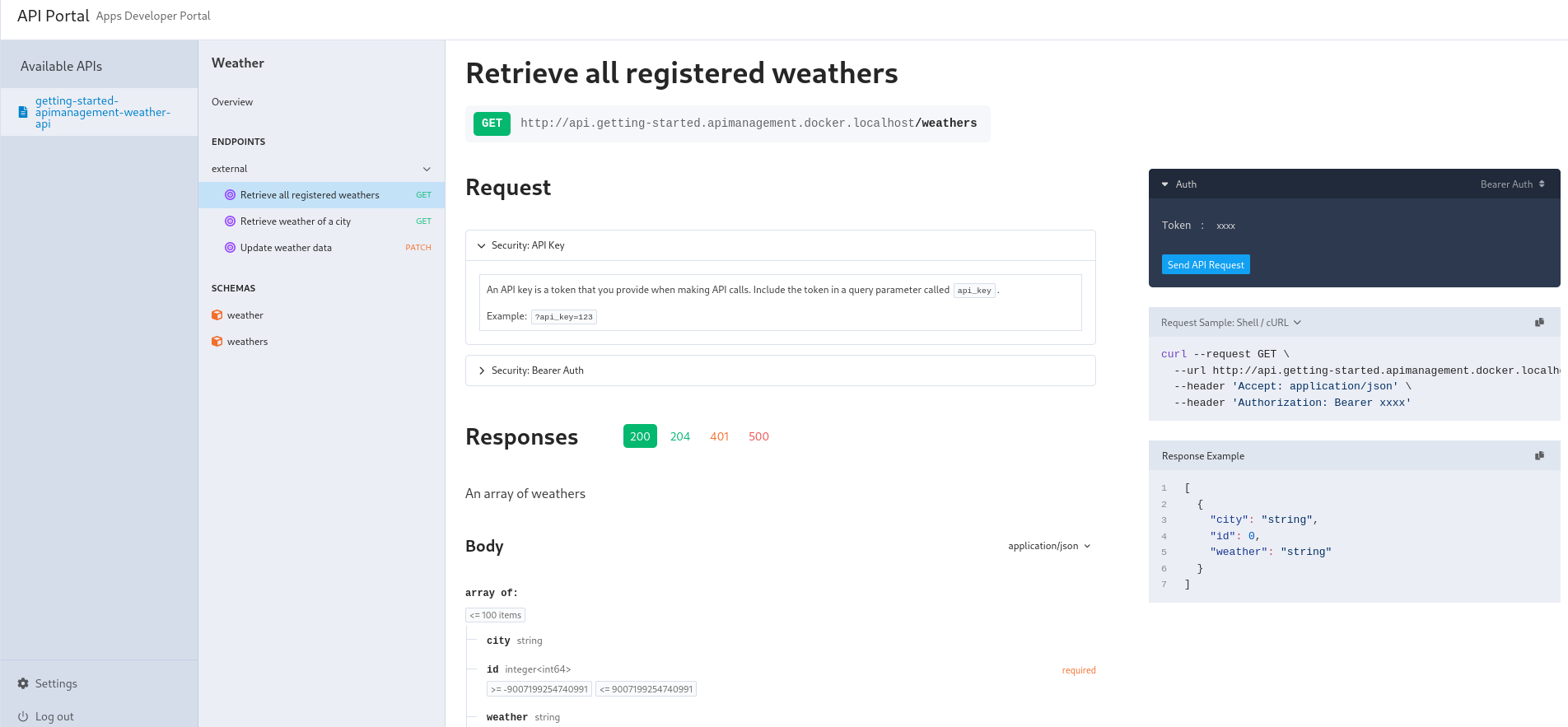
The Weather API has documentation built from the OpenAPI specification, and the API can also be interactively tested right on the Portal with the try-out functionality.
And that's it! You’ve now seen the very short and quick upgrade steps of each tool and also got a glimpse of using them.
Wrapping It Up
The seamless migration journey across Traefik Labs' products ensures that everything built remains intact while adding new capabilities as needed. Investing time and resources into Traefik Proxy, Traefik Hub API Gateway, or API Management is a smart choice for businesses looking to future-proof their infrastructure. There is no rip-and-replace—just an in-place upgrade!
Consider Traefik’s cloud-native, fully declarative, and GitOps-driven approach to ensure efficient and effective API operations in your organization. The functionally additive upgrade path, robust feature set, and ease of management make it the best choice for handling the complexities of modern cloud-native environments. Scale your operations confidently with Traefik as your business grows and evolves.
In This Article
- Start With Us and Grow With Us
- Traefik Proxy: Born in The Trenches
- Journey Lab 1: Deploy a Weather Service with Traefik Proxy
- Traefik Hub API Gateway: Level Up Your API Security
- Journey Lab 2: Upgrade Traefik Proxy to Traefik Hub API Gateway
- Traefik Hub API Management: Granular Control and Scalability
- Journey Lab 3: Upgrade Traefik Hub API Gateway to API Management
- Wrapping It Up




